-
SchermGeheugenGewichtProcessorHard DiskSSDSchermResolutieConnectiviteitGeheugenDesktopOSSchermTypeSnelheid ZwartSnelheid KleurenModelSnelheidVorm factorInterne / ExterneAantal poortenUplink / mediaMontage
- Alles bekijken
Bundles
Verwante producten
Product Informatie
The world's best visibility, protection, and response.
See it. Stop it. Secure it.
Expose Hidden Risks
Superior visibility into risky activity, suspicious traffic, and advanced threats helps you regain control of your network.
Stop Unknown Threats
Powerful next-gen protection technologies like deep learning and intrusion prevention keep your organization secure.
Isolate Infected Systems
Automatic threat response instantly identifies and isolates compromised systems on your network to stop threats from spreading.
Secure Remote Workers
XG Firewall makes it easy to extend your secure network to employees anywhere.
Free, Easy-to-Use VPN Client
Sophos Connect provides an intuitive VPN connection client that’s easy to deploy and configure. Give your remote workers secure access to resources on the corporate network from Windows and macOS devices.
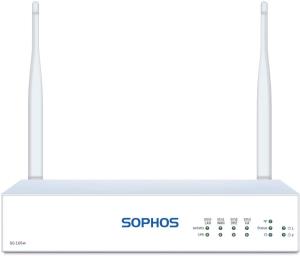
SOHO Protection with XG 86 or SD-RED
Our small, ultra-affordable XG 86(w) and SD-RED devices provide the ultimate in SOHO protection with always-on dedicated or split-tunnel VPN that’s easy to deploy and manage with a variety of flexible options.
Mobile VPN
Mobile devices can utilize built-in or app-based VPN options including IPSec and SSL VPN for secure connectivity to your XG Firewall protected network.
XG Firewall’s all-new Xstream architecture delivers extreme levels of visibility, protection, and performance.
XG Firewall Xstream TLS Inspection
Industry-leading performance and visibility into all the encrypted traffic on your network with support for TLS 1.3
XG Firewall Xstream DPI Engine
High-performance deep packet protection in a single streaming engine for stopping all known and unknown threats
XG Firewall Xstream Network Flow FastPath
Accelerate trusted and important cloud, SaaS, and VoIP application traffic for optimal performance
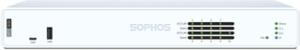
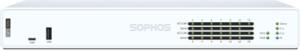
XG Series Appliances
The ultimate in performance, flexibility, and connectivity.
Our XG Series hardware appliances are purpose-built with the latest multi-core processors, generous RAM provisioning, solid-state storage, and flexible connectivity options.
Whether you’re protecting a small business or a large datacenter, you’re getting industry-leading price: performance, and the ultimate in flexibility, connectivity, and reliability in every form factor.
Synchronize Your Firewall and Endpoint Security
XG Firewall is part of the world’s best cybersecurity system, integrating in real time with Intercept X.
100% Application Visibility
Identify all unknown applications on the network.
Monitor Health and Threats
Instantly identify compromised hosts.
Automatic Threat Isolation
Stop breaches and isolate infected endpoints instantly, blocking lateral movement.
Central Cloud Management
One Console to Manage It All
Easily make a change to one firewall and push it out to others with just a few clicks using the new Group Firewall Management tools in Sophos Central.
Reporting in the Cloud
Sophos Central now includes flexible reporting tools that enable you to visualize your network activity and security over time. You get several built-in reports as well as easy tools to create your own custom reports.
Zero-Touch Deployment
Easily deploy new XG Firewall devices from Sophos Central without having to touch them.
Complete Next-Gen Protection
All the advanced networking, protection, user, and app controls you need to stay secure and compliant.
Management
Firewall management
XG Firewall provides an elegant and effective web-based management console and integrates with Sophos Central for powerful cloud management across your entire network and Sophos product portfolio.
- Sophos Central provides the ultimate cloud management platform for all your Sophos products including XG firewall at no extra charge.
- Group Firewall Management in Sophos Central enables you to make policy, setting, or object changes across your entire estate of XG Firewalls with just a few clicks.
- Central Firewall Reporting provides easy insights into threats, compliance, and user activity across your entire network with flexible tools to build your own reports and views.
- XG Firewall’s Control Center provides at-a-glance feeds of system performance, traffic patterns, alerts, and policies.
- Role-based admin provides flexible granular access control for different functional areas and Sophos Central allows you to control which admins have access to which firewalls.
Centralized Management
Sophos Central provides powerful centralized management, reporting, and zero-touch deployment for all your XG Firewalls and other Sophos products from a single console.
- Sophos Central is the ultimate cloud-management platform - for all your Sophos products. It makes day-to-day setup, management, and reporting for all your XG Firewalls easy. It is free of charge for all XG Firewall customers.
- Sophos Central Firewall Management includes powerful cloud-based group firewall management, backup management, one-click firmware updates and rapid zero-touch provisioning of new firewalls.
- Sophos Central Firewall Reporting provides flexible reporting in the cloud for all your XG Firewalls with easy tools to create your own custom reports.
Status and Alerts
The all-new, carefully crafted control center analyzes extensive back-end data sources to surface just the information you need to respond quickly to changes in your network.
- Instant insights at a glance for all your important system, security and network status indicators from the all-new control center
- Automated report analysis highlights reports in the control center featuring data of interest or that may need attention, with one-click access to the full report.
- Quick drill-down interaction with any control center widget to get more detailed information, access relevant tools, or quickly take action.
- Email notifications are automatically sent for important system status events.
- SNMP with a custom MIB and support for IPSec VPN tunnels to manage remote office firewall devices.
Reporting and Logging
Take advantage of the XG Firewall’s extensive on-box reporting or utilize Central Firewall Reporting for comprehensive, centralized reporting across your entire network.
- On-box reporting comes standard at no extra charge with every XG Firewall for all your local firewall reporting needs.
- Central Firewall Reporting provides flexible reporting in the cloud for all your XG Firewalls with easy tools to create your own custom reports and then save, schedule or export them.
- User and app risk analysis reports such as our unique User Threat Quotient or App Risk Score identify top risk users and applications respectively.
- Live log viewer, accessible from any screen, provides a real-time view into activity in your firewall across all areas of the firewall with powerful search and filter options.
- Syslog support enables safe export, backup, archival, and integration with 3rd party reporting solutions.
USER AND APP CONTROL
User Identity
User identity-based policies and unique user risk analysis give you the knowledge and power to regain control of your users before they become a serious threat to your network.
- User identity powers all firewall polices and reporting, enabling unprecedented next-gen control over applications, web surfing, bandwidth quotas, and other network resources.
- User Threat Quotient (UTQ) identifies the top risk users on your network based on their recent network behavior.
- Synchronized User ID – a unique Sophos Synchronized Security feature eliminates the need for client or server authentication agents by sharing user identity between the endpoint and the firewall through Security Heartbeat™.
- Flexible authentication options including directory services (AD, eDirectory, LDAP), Kerberos, NTLM, RADIUS, TACACS+, RSA, client agents (including Chromebook support), or captive portal.
- Two-factor authentication (2FA) one-time password support for access to key system areas, including IPsec and SSL VPN, the user portal, and the web administration console.
Application Control
Complete application visibility and control over all applications on your network with deep-packet scanning technology and Synchronized App Control that can identify all the applications that are currently going unidentified on your network.
- Visibility and control over thousands of applications via customizable policy templates with granular controls and smart filter lists that enable you to build custom policies based on category, risk, technology, or other characteristics.
- CASB cloud app visibility identifies all browser applications and cloud services to identify Shadow IT and data at risk to get it under control quickly and easily.
- Synchronized App Control provides a breakthrough in network visibility by identifying all the applications that are unknown, unidentified, or generic on your network enabling you to classify and control them. Prioritize the apps you want and block the ones you don’t.
- User-based application policies enables custom-tailored application control to be added to any user, group, or network policy with the option to also apply traffic shaping.
- Traffic shaping (QoS) prioritizes bandwidth allocation to critical applications and limits bandwidth for non-business applications.
Web Control
Full visibility and control over all your web traffic with flexible enforcement tools that work the way you need, with options for user and group enforcement of activity, quotas, schedules, and traffic shaping.
- Enterprise Secure Web Gateway (SWG) policy model with hierarchical inheritance enables sophisticated group and user-based web filtering policies to be defined quickly and easily, dramatically reducing firewall rule count.
- Template-driven activity control with predefined workplace and compliance policies utilize over 90 predefined website categories, covering billions of pages maintained by SophosLabs with the option to import custom URL lists.
- Education features like YouTube restrictions and SafeSearch as well as temporary web policy overrides controlled by teachers provides flexible, powerful, but easy to use compliance controls.
- Comprehensive enforcement monitors HTTPS encrypted traffic, blocks anonymizing proxies, and can enforce Google Apps domains ensure your policies are always enforced.
- Traffic shaping (QoS) prioritizes bandwidth allocation to critical web applications and limits bandwidth for non-business websites.
Content Control
Flexible, user-based monitoring and control of keyword content and downloadable content, including files types via FTP, HTTP, or HTTPS.
- Web keyword monitoring can log and dynamically block content matching uploaded keyword libraries regardless of the site category to help identify problematic or risky behavior related to topics like self-harm, radicalization, bullying, and more.
- File download filtering templates let you control hundreds of different files, executables, and dynamic content types simply as part of any user or network web control policy.
- Outbound email DLP that's policy-based can automatically trigger encryption or block/notify based on the presence of sensitive data in emails leaving the organization.
- Web caching reduces bandwidth consumption by caching supported web content and downloads, including Sophos Endpoint updates.
Protection
Deep Packet Inspection
The Xstream Deep-Packet Inspection (DPI) engine provides high-performance traffic scanning for IPS, AV, Web Protection and App Control in a single streaming engine.
- Industry leading TLS 1.3 Inspection provides high-performance policy based decryption of encrypted traffic flows to remove an enormous blind-spot.
- Advanced next-gen Intrusion Prevention System (IPS) protection combining signatures from SophosLabs and 3rd parties provides the ultimate network exploit prevention, protection and performance.
- Zero-day Threat Protection applies machine learning analysis and cloud sandboxing to any content with active code to block the latest zero-day threats and ransomware before they get on the network.
- Proxy-based dual-engine AV scanning offers the option of scanning traffic with the Sophos engine for excellent performance and protection, or adding a second engine scan for even more protection.
- Perimeter defenses stop attacks on your network, including reconnaissance detection, spoofing, flood protection (DoS, DDoS), and packet-based attacks (ICMP).
- Country-based policy blocks Geo IP ranges for entire countries or regions.
Cloud Sandbox
Sophos Zero-day Dynamic File Analysis uses next-gen cloud-sandbox technology powered by deep-learning and the best technology from Intercept X, to provide your organization with the best protection against zero-day threats like the latest ransomware and targeted attacks coming in through phishing, spam, or web downloads.
- Cloud delivery means our sandboxing is fully integrated with your XG Firewall and requires no additional hardware and doesn’t impact performance at all.
- Identifies suspicious payloads such as PDFs, Office Docs, and executables entering the network via email or the web and sends those to the cloud sandbox for extensive machine learning based analysis and remote execution to convict zero-day payloads before they enter your network.
- Powered by deep learning and the best technologies from our leading Intercept X next-gen endpoint product, including exploit detection and CryptoGuard protection, stops zero-day threats before they get on your network.
- Great value, affording you all the benefits of enterprise-grade protection without the enterprise price tag.
- Detailed threat reports for every incident so you know exactly what’s going on.
Zero-Day and ML Protection
Sophos XG Firewall leverages Sophos’ industry leading, machine learning technology, powered by SophosLabs Intelix .
- Threat intelligence comes from our critically acclaimed global Tier-1 threat research lab, SophosLabs leveraging the industry’s top data scientists and extensive research into predictive deep-learning analysis and detection.
- Multiple Machine Learning Models utilize artificial neural networks and advanced learning techniques to analyze new files against a database of millions of good and bad known files to convict new zero-day malware variants and threats.
- Static File Analysis leverages the power of these multiple machine learning models, global reputation, deep file scanning, and more without needing to execute the file in real time.
- Dynamic File Analysis detonates files in real-time in a sandbox utilizing the latest analysis techniques and threat detection technologies from Intercept X for unmatched visibility into new or emerging malware and ransomware.
Web Protection
Sophos' Web Protection engine is backed by SophosLabs and includes innovative technologies required to identify and block the latest web threats.
- Advanced Web Protection combines advanced analysis capabilities such as JavaScript emulation, behavioral analysis, and origin reputation to protect against modern, multi-stage web attacks.
- Pharming protection guards against phishing and pharming attacks by overriding corrupt host file or DNS lookups.
- HTTPS scanning deep scans encrypted traffic for threats and compliance.
- Potentially unwanted app control protects your network from cryptomining and cryptojacking embedded in websites as well as a variety of other unwanted web borne applications.
- SophosLabs, the global, round-the-clock threat research operation, identifies thousands of newly infected websites and instances of web malware, ensuring you have the best malicious site database protecting your network and users.
Synchronized Security
Our revolutionary Security Heartbeat™ links your Sophos managed endpoints with your firewall to deliver unparalleled protection from advanced threats while significantly reducing the time and complexity of responding to security incidents.
- Security Heartbeat: XG Firewall monitors the Security Heartbeat status of all your Sophos endpoints, enabling you to quickly identify compromised systems and automatically limit network access for these systems until they can be cleaned up.
- Destination Heartbeat Protection controls access to endpoints and servers based on the status of their Heartbeat – further bolstering protection from potentially compromised systems until they are completely safe.
- Synchronized App Control a breakthrough in network visiblity, utilizes the Synchronized Security relationship to automatically identify, classify and control unknown applications on your network.
- Lateral Movement Protection automatically isolates compromised systems at every point in the network to stop attacks dead in their tracks. Healthy endpoints assist by ignoring all traffic from unhealthy endpoints, enabling complete isolation, even on the same network segment, to prevent threats and active adversaries from spreading or stealing data.
- Synchronized User ID eliminates the need for client or server authentication agents by sharing user identity between the endpoint and the firewall through Security Heartbeat™
Advanced Threat Protection
XG Firewall delivers advanced threat protection to instantly identify bots and other advanced threats while defending your network from today’s sophisticated attacks.
- Security Heartbeat links your endpoints and your firewall, combining their intelligence to identify and isolate systems compromised by advanced and previously unknown threats.
- Multi-layered, call-home protection combines analysis from DNS, IPS, web, and traffic filters to identify and block botnet and command-and-control (C&C) call-home attempts.
- Intelligent firewall policies account for endpoint behavior to automatically isolate or limit access to infected systems that may be compromised by an advanced threat.
- Traffic light style indicators provide immediate identification of systems at risk with deep drill down into the device, user, and process responsible.
Business Applications
Combine next-gen firewall capabilities with our enterprise-class web application firewall to protect your critical business applications from hacks and attacks while still enabling authorized access.
- Next-generation IPS provides advanced protection from hacks and attacks while maintaining top performance.
- Web Application Firewall integrates seamlessly with your next-gen firewall, combining industrial-strength protection like URL and form hardening with the ease of template-driven policy configuration.
- Granular, user-based protection with a rich set of configuration options and multiple authentication options, ensuring easy access for those you want and powerful protection from those you don't.
Email and Data
Protect your email from spam, phishing, and data loss with our unique all-in-one protection that combines policy-based email encryption with DLP and anti-spam.
- Full MTA store and forward support enables business continuity, allowing the firewall to store mail when target servers are unavailable.
- Live anti-spam provides protection from the latest spam campaigns, phishing attacks, and malicious attachments.
- SPX encryption is unique to Sophos, making it easy to send encrypted email to anyone, even those without any kind of trust infrastructure.
- DLP that's policy-based can automatically trigger encryption or block/notify based on the presence of sensitive data in emails leaving the organization.
- Self-serve user portal gives employees direct control over their spam quarantine and block/allow lists, saving you time and effort.
Networking
NAT, Routing & Bridging
Protect your email from spam, phishing, and data loss with our unique all-in-one protection that combines policy-based email encryption with DLP and anti-spam.
- Full MTA store and forward support enables business continuity, allowing the firewall to store mail when target servers are unavailable.
- Live anti-spam provides protection from the latest spam campaigns, phishing attacks, and malicious attachments.
- SPX encryption is unique to Sophos, making it easy to send encrypted email to anyone, even those without any kind of trust infrastructure.
- DLP that's policy-based can automatically trigger encryption or block/notify based on the presence of sensitive data in emails leaving the organization.
- Self-serve user portal gives employees direct control over their spam quarantine and block/allow lists, saving you time and effort.
Segmentation
Flexible and powerful segmentation options via zones and VLANs provide ways to separate levels of trust on your network while enabling added protection against lateral movement between different parts of your network.
- Zones rise above the traditional interface-based configuration model to provide a more intuitive, powerful, and simple way to secure and segment your network and create policy.
- Default zones for LAN, WAN, DMZ, LOCAL, VPN, and Wi-Fi make it easy to get up and running quickly and easily with support for custom zones on the LAN or DMZ.
- Full VLAN support provides powerful segmentation options by trust, traffic type, location, and other criteria across your physical network infrastructure.
- Zone and VLAN isolation ensures zones are isolated until firewall rules are explicitly created to enable secure exchange of application, user, and network traffic to pass between them.
- Zone-based policies enable simple but powerful firewall rules that anyone can immediately interpret and understand.
Traffic Shaping
Flexible and powerful but easy-to-use traffic shaping (also known as quality of service or QoS) controls enable configuration by application, category, user, group, or policy rule.
- Network or user-based traffic shaping prioritizes bandwidth allocation to critical applications and limits bandwidth for non-business applications on any network or user-based policy.
- Web category traffic shaping prioritizes bandwidth allocation and/or limits based on website category.
- Network traffic quotas allow unlimited customization for total or individual network traffic quotas.
- Real-time VoIP optimization ensures real-time traffic for Voice over IP and other communications are given prioritization.
Wireless Controller
Integrated wireless controllers in XG Firewalls enables easy secure wireless deployments managed from a single console.
- Plug-and-play deployment enables quick installation and configuration with just a few clicks since the firewall automatically recognizes the Sophos Wireless Access Point as soon as it’s connected.
- High performance with the latest 802.11ac, Wave 2 wireless standard, and powerful radios, offering maximum coverage and throughput.
- Flexible configuration with options for isolation, bridging, zones, hotspots, channel width, and multiple SSIDs per radio.
- Secure encryption with support for all the latest standards including WPA2 personal and enterprise.
Performance
Sophos XG Firewall offers among the highest price per protected Mbps of any firewall on the market thanks to the new Xstream packet-processing architecture, DPI engine and TLS 1.3 inspection.
- Xstream DPI Engine with high-performance deep packet protection in a single streaming engine for stopping all known and unknown threats.
- Xstream TLS Inspection with industry-leading performance and visibility into all the encrypted traffic on your network with support for TLS 1.3.
- Xstream Network Flow FastPath accelerates trusted and important cloud, SaaS, and VoIP application traffic for optimal performance.
- High-Performance XG Series Appliances with high-speed interfaces and connectivity come with plenty of GigE ports on every appliance and optional FlexiPort expansion modules for added performance over copper or fiber.
- High availability with active-active load balancing or active-passive fail-over and WAN link balancing lets you easily double your performance when you need it.
VPN and SD-RED
XG Firewall makes it easy to extend your secure network to employees anywhere. Select from a full range of VPN technologies and our unique SD-RED branch office devices for secure site-to-site and remote access.
- Full standards-based VPN support includes IPSec (with IKEv2 support), SSL, PPTP, L2TP, Cisco VPN (iOS), and OpenVPN (iOS and Android).
- Sophos Connect Remote Access VPN client enables easy bulk deployment of SSL or IPSec VPN on Windows and Macs for remote workers.
- Free Remote Access VPN connections up to the capacity of your device.
- Clientless portal using Sophos' unique encrypted HTML5 self-service portal provides support for RDP, SSH, Telnet, and VNC for quick access to essential business applications.
- SD-RED VPN a Sophos exclusive, provides a robust light-weight layer 2 site-to-site VPN option between firewall devices or using our affordable SD-RED (Remote Ethernet Device) at the remote site to easily establish a secure VPN connection.
SD-WAN
XG Firewall integrates essential SD-WAN features and capabilities like multiple link monitoring and fail-over and fail-back, application path selection and routing, and unique zero-touch SD-RED remote devices for SOHO and branch office deployments.
- Multiple WAN link options including VDSL, DSL, cable, and 3G/4G/LTE cellular with essential monitoring, balancing, and failover
- Application path selection and routing, which is used to ensure quality and minimize latency for mission-critical applications such as VoIP
- Synchronized SD-WAN leverages the added clarity and reliability of application identification that comes with the sharing of Synchronized Application Control information between Sophos-managed endpoints and XG Firewall
- Application routing over preferred links via firewall rules or policy-based routing
- SD-RED Devices provide the ideal solution for securing remote devices or SOHO or small branch office locations by providing a zero-touch affordable device that supports our unique Layer 2 RED site-to-site tunnel and split-tunnel operation
Encrypted Traffic
Xstream TLS Inspection with industry-leading performance and visibility into all the encrypted traffic on your network with support for TLS 1.3.
- Xstream TLS inspection with high performance, support for TLS 1.3 with no downgrading to TLS 1.2
- Port-agnostic able to scan traffic across all ports and protocols - not limited to HTTPS on port 443
- Enterprise policies with granular controls over what to decrypt to optimize privacy, protection, and performance for your particular needs.
- Unique dashboard visibility, and compatibility troubleshooting to identify users and sites having difficulties with TLS inspection with one-click options to exclude problematic sites.
| Data-uitwisseling | |
| Firewall-doorvoersnelheid | 3,55 Gbit/s |
| Firewall (IMIX) doorvoercapaciteit | 2 Gbit/s |
| IPSec-VPN-doorvoercapaciteit | 0,33 Gbit/s |
| Bedreigingsbeveiliging doorvoer | 150 Mbit/s |
| Xstream SSL-ontsleuteling + Bedreigingsbeveiliging | 75 Mbit/s |
| SSL-inspectie doorvoercapaciteit | 75 Mbit/s |
| Maximum firewall verbindingen per seconde | 14700 |
| Prestatie | |
| Warmtedissipatie | 35,6 BTU/h |
| Warmteafvoer (onbelast) | 30,28 BTU/h |
| Antennas quantity | 2 |
| Soort antenne | 2x2 |
| Concurrent connections | 1570000 |
| Reset button | Ja |
| MIMO | Ja |
| Certificering | CB, CE, FCC, ISED (IC), VCCI, RCM, UL, CCC, BIS, Anatel |
| Netwerk | |
| Wifi | Ja |
| Wi-Fi-standaarden | 802.11a, 802.11b, 802.11g, Wi-Fi 4 (802.11n), Wi-Fi 5 (802.11ac) |
| Gelijktijdige SSL/VPN-verbindingen (maximaal) | 8192 |
| Beheerfuncties | |
| LED-indicatoren | Activiteit, LAN |
| Poorten & interfaces | |
| Connectiviteitstechnologie | Bedraad en draadloos |
| Aantal USB 2.0-poorten | 2 |
| Aantal Ethernet LAN (RJ-45)-poorten | 4 |
| Ethernet LAN, data-overdrachtsnelheden | 100,1000 Mbit/s |
| Console port | RJ-45 |
| Aantal HDMI-poorten | 1 |
| Aantal micro-USB-poorten | 1 |
| Aantal moduleslots SPF | 1 |
| Opslagmedia | |
| Opslagmedia-type | SSD |
| Design | |
| Rack-montage | Ja |
| Vormfactor | Desktop |
| Energie | |
| AC-ingangsspanning | 100-240 V |
| AC-ingangsfrequentie | 50 - 60 Hz |
| DC voltage input | 12 V |
| Vermogensverbruik (max) | 10,44 W |
| Stroomverbruik (idle) | 8,88 W |
| Netvoeding | 36 W |
| Redundante voeding | Ja |
| Logistieke gegevens | |
| Land van herkomst | Taiwan |
| Code geharmoniseerd systeem (HS) | 85176990 |
| Eisen aan de omgeving | |
| Bedrijfstemperatuur (T-T) | 0 - 40 øC |
| Temperatuur bij opslag | -20 - 80 øC |
| Relatieve vochtigheid in bedrijf (V-V) | 10 - 90 procent |
| Luchtvochtigheid bij opslag | 10 - 90 procent |
| Gewicht en omvang | |
| Breedte | 153,2 mm |
| Diepte | 245 mm |
| Hoogte | 44 mm |
| Gewicht | 1,23 kg |
| Verpakking | |
| Breedte verpakking | 224,5 mm |
| Hoogte verpakking | 133 mm |
| Gewicht verpakking | 2,47 kg |
| Inhoud van de verpakking | |
| Meegeleverde kabels | AC |
| Overige specificaties | |
| Firewall throughput | 3550 Mbit/s |
| Warranty | |
| Base Warranty | Non Non |